Managed Cyberdefence services
Managed SOC
A complete security incident detection and response service
Alter Solutions' Managed Security Operations Center leverages the latest technological advances (Artificial Intelligence) and our experience to improve your detection capabilities, accelerate your incident response and reduce your costs.

Alter Solutions' security incident response line : +33 1 87 66 97 36
What is Managed SOC?
Alter Solutions’ Managed SOC provides cybersecurity expertise to monitor your IT infrastructure, protecting it against all kinds of threats and cyberattacks, on a 24/7 basis (SOC-as-a-Service). This service covers cloud environments, devices (including mobile), users, logs, networks, e-mails, and so on.
Our Managed SOC solution can also serve as an expansion of your existing SOC team – you’ll have direct access to our analysts, who work alongside your security team.
A Managed SOC service is perfect for organisations that want to improve their cybersecurity posture, but lack the resources, expertise, time and/or budget to do it in-house.
Why Alter Solutions' Managed SOC?
Improve your detection and incident response capabilities
Build a powerful detection service in record time by leveraging our proven experience with processes and tools for collection, analysis, investigation, and incident response.
Control your costs
Benefit from the resources you need at a controlled cost, including security software solutions and their integration, operational maintenance and detection, and, of course, all the cybersecurity expertise available 24/7.
Adopt a flexible solution
We are technologically agnostic, which means we can lift your existing security solutions to their full potential or assist you in choosing partner solutions that can best fit your security needs.
Access the latest technologies
Our team intervenes with the support of a single platform that includes sophisticated approaches and technologies like SOAR, SIEM, EDR, among others. We are also able to integrate your own solutions in the way we work.
Save time and resources
Implementing a great cybersecurity strategy takes a lot of focus and expertise. That means time, money, and resources. By hiring a Managed SOC, you can guarantee that your information system is in good hands and complies with major cybersecurity regulations, while keeping your internal team focused on other important tasks.
Control your security and data
When outsourcing a Managed SOC service, organisations may fear losing control over their security strategy and their sensitive data. With our service, you’ll be able to follow what’s happening in real-time, you’ll be informed if any threat arises, and the ultimate decision on how to act is still yours. Also, our SOC team won’t need to have full access to your sensitive data to keep it safe.
Understanding the Managed SOC process
Our Managed SOC service comprises the following phases:

All four phases - Prevention, Detection, Investigation and Response - of the Managed SOC service operate in a continuous and integrated manner, based on an Agile, dynamic and iterative model, which enables constant monitoring and effective security incident remediation.
Our Managed SOC experts work collaboratively every step of the way to make sure everything runs smoothly and has no impact at all on your business operations.
So what characterises each of the four phases?
Prevention
Continuous improvement of detection rules
We constantly update our detection rules according to threat evolution and the environments of our customers.
Automatic threat blocking
Implementation of automatic responses on high-fidelity use cases (without false positives).
Technology consulting
We provide our clients with our expertise in cyberdefense to guide them in their technological choices.
Detection
24x7 Detection
Take advantage of our continuous detection capabilities for a fast and effective response.
The right data, at the right time
Advice on the collection strategy to adopt and support in its implementation.
Advanced detection methods
Artificial Intelligence, Machine Learning, UEBA, weak signal detection, Threat Intelligence.
Investigation
Contextualization
Alerts are automatically enriched with data allowing for context and quick response.
Qualification
Sorting of true and false positives and determination of the criticality of the alert.
Deep investigation
When necessary, a manual investigation is performed by our experts to conduct an in-depth analysis and report.
Response
Fast response and automated acceleration
Response performed by our experts and supported using our SOAR platform.
Incident response tracking
Proven incident reporting and tracking process allowing customers to track all stages of the response.
Our SOC models
SOC-as-a-Service (fully outsourced)
We manage your cybersecurity operations entirely, from our own security centre, with our complete team of experts.
Hybrid SOC
You maintain your own security team and centre at the forefront, and we reinforce them with whatever resources and expertise you need.
Our Managed SOC teams
- Operation of security tools
- Elementary incident analysis
- Creation of investigation file
- Alerts qualification
- Reporting on low critical alerts
- Continuous improvement of the service
- Detection rules creation
- Emerging technology monitoring
- Investigation on qualified security incidents
- Reporting on critical security incidents
- Development of remediation plans
- Main client contact
- Contract management
- Quality control of the service
- Leader of regular reporting meetings
- Collection and analysis of threat intelligence from internal and external sources
- Presenting actionable intelligence to SOC teams for proactive defence
- Maintaining threat intelligence platforms and contributing to threat reports
- Analysis of malware samples to understand their behaviour and impact
- Development of detection and mitigation strategies for identified threats
- Sharing findings with SecOps Engineers to improve defence mechanisms

While most SOCs use Level 1 analysts for alert monitoring, triaging, and documentation, Alter Solutions uses AI and advanced tools to automate these tasks. This allows us to detect threats faster, reduce false positives, and free our analysts to focus on strategic activity.
Unified security detection
Our Managed SOC services feature a network of interconnected security tools, which use integrated connectors to enhance communication and shared detection capabilities. This setup provides a comprehensive view of security threats, enabling more effective identification and assessment. Those security tools are:

SIEM
Security Information and Event Management (SIEM) is a software solution that provides a comprehensive view of organisations’ IT security. It allows them to identify and address security vulnerabilities and threats before they get a chance to disrupt business operations.
SOAR
Security Orchestration, Automation, and Response (SOAR) is a technology stack that automates cybersecurity incident response processes within a single platform.
EDR
Endpoint Detection and Response (EDR) is a cybersecurity solution focused on detecting and investigating threats on endpoint like laptops, desktop computers, servers, and mobile devices.
NDR
Network Detection and Response (NDR) is a cybersecurity solution that detects and responds to cyber threats on corporate networks, leveraging Machine Learning (ML), Artificial Intelligence (AI) and data analytics.
UEBA
User and Entity Behavior Analytics (UEBA) is a cybersecurity software specialised in analysing users and entities’ behavior within an organisation’s network and infrastructure, in order to detect suspicious activities and address insider threats.
Choose the service level for your needs
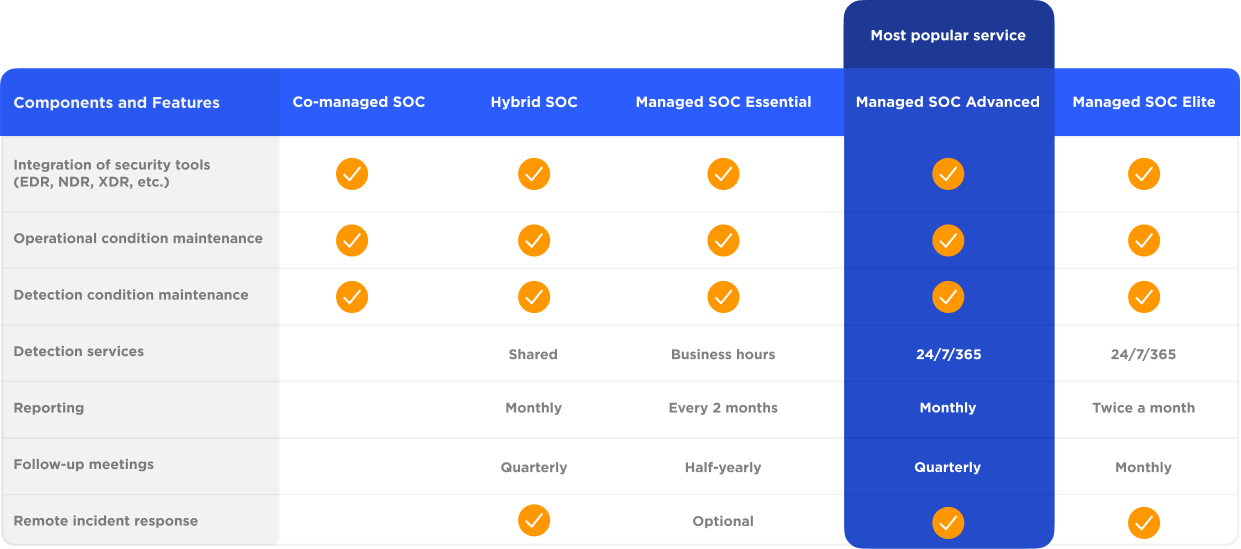
For each service level, we can also provide on-site incident response on demand.
Why Alter Solutions?
18 years of experience
Alter Solutions was founded in Paris, in 2006, and has since focused on digital transformation. We operate in 8 countries across Europe, America and Africa, and we have been security partners for companies in the manufacturing, service, finance, insurance, transport, and technology sectors for over 10 years.
Flexibility and customer-centric approach
We provide a level of service tailored to the client's needs, going all the way to a 24/7 protection. We have a strong track record across different sectors and technologies, and our approach to IT services is technology agnostic – what's right for each customer is what counts.
Privacy as a core value
Both yours and your customers’ data is safe with us. Our SOC experts operate within the European Union (EU), meaning we fully comply with the General Data Protection Regulation (GDPR).
Key certifications
We hold relevant security certifications like ISO 27001, CSIRT and PASSI. Our experts are also certified with GCIH, GCTI, GCFA, GCIA, SANS and OSCP.
Other Managed Security Services
We cover all your organisation’s security needs with other managed security services
FAQ
A Security Operations Center (SOC) is a centralised cybersecurity team responsible for actively monitoring, preventing, detecting, analysing, and responding to cybersecurity threats in real-time, preferably 24/7.
A SOC can be an in-house, a hybrid or a fully outsourced team of cybersecurity experts. It usually includes SOC Analysts, SecOps Engineers, Incident Responders, Service Delivery Manager, Threat Intelligence Analysts and Malware Analysts.
The SOC team as a whole is responsible for managing an organisation’s security operations and for improving its overall security posture. These professionals perform tasks such as: security tools management, threat monitoring, threat prevention, cyber incident investigation and response, data/assets recovery, reporting, compliance, among other things.
SOC-as-a-Service (SOCaaS) is a fully outsourced Managed SOC. It means that an organisation’s SOC is set up by an external provider, whose experts work remotely and take care of the company’s whole cybersecurity operations.
Outsourcing a SOC will always represent cost-savings, when compared to investing in an in-house team to do the same job 24/7. This solution will also help your company improve its cybersecurity posture, enhance detection and incident response skills, access the most sophisticated cyber technologies and tools, while saving time and internal resources to focus on core business activities.
The cost of a Managed SOC service varies widely based on the organisation's size, required services, and level of coverage, among other factors. We offer tailored solutions to meet your specific needs, so for an accurate estimate, please reach out to us.




